SAML 2.0
Infiniti supports SAML 2.0 allowing a nominated identity provider enabling Single sign-on (SSO) between Infiniti Manage and Produce and other service providers. Common SAML 2.0 implementations implement Infiniti forms within another application.
When configured correctly, when navigating to Infiniti a request is sent to the identity provider via HTTP-POST. The identity provider will determine whether the user has already been authenticated or requires login. Regardless after a successful login has occurred a response is sent to Infiniti containing the user’s username (referred to as NameId which is a required field) and optionally other user profile information (name, email, address, group memberships, etc.). The response must be signed so that Infiniti knows it is from a trustworthy source.
Prerequisites
An existing Infiniti environment installed with default forms authentication.
A SAML 2.0 provider with ◦An Identity Provider (Idp) configured to
- Return a group memberships as an assertion attribute (e.g. IsMemberOf) (mandatory to ensure at least one user can be added to an Infiniti Administrator Role after the switch to SAML) within the SAML assertion
- Return profile information such as first and last name (Optional)
Service Providers for both Infiniti Manage and Infiniti Produce whereby:
- The response is configured to be sent via HTTP-POST to: http://yourserver/Manage/SamlAuthenticate.aspx or http://yourserver/Produce/SamlAuthenticate.aspx respectively
- The above post response is signed (see Appendix A for an example Response)
- A meaningful name is given to the Service Providers (usually Produce and Manage)
- A certificate either installed on the Infiniti web server or uploaded as file that can be used to check the SAML response signature (I.e. the certificate used by the IdP to sign the response).
- A user configured in the SAML 2.0 provider for testing that is a member of at least one known group.
How to configure SAML 2.0
By default Infiniti Installations use Forms Authentication as the licensing and an administrator group must be configured before SAML can be configured.
Step 1 - Identify an SAML Infiniti Administrator Group
When the first user (usually a server administrator) attempts to access Infiniti via SAML Authentication, Infiniti needs to assign permissions so they can access appropriate functions. If this step is not completed users will be not be able to actually do anything post authentication.
When the first user (usually a server administrator) attempts access, Infiniti needs to assign them permissions so they can access appropriate functions. If this step is not completed users will not be able to actually do anything post authentication. Use the article below to configure an external group
Step 2 - Enable and Configure SAML
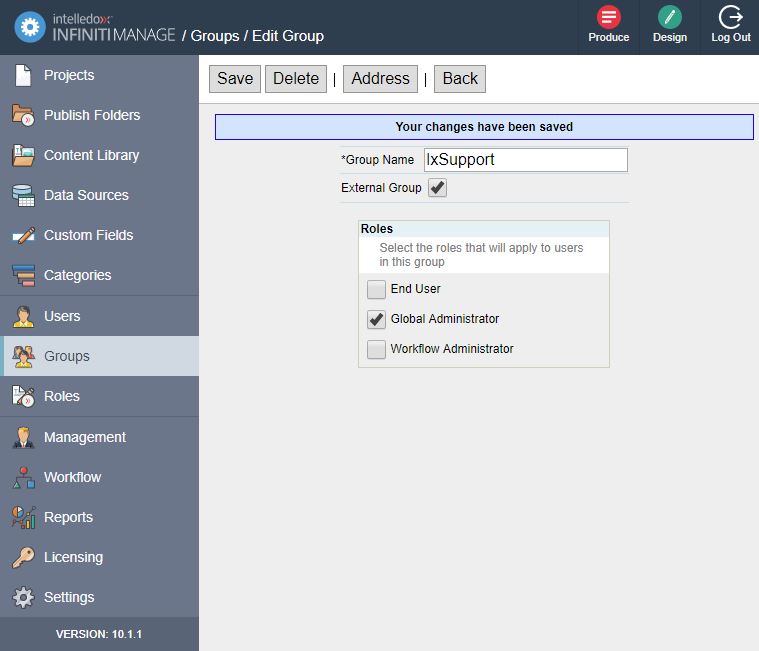
- Navigate to Settings and 'New Group' and click the SAML 2.0 Tab
- Check the SAML 2.0 checkbox and configure the now enabled settings as per the screen shot and table below.
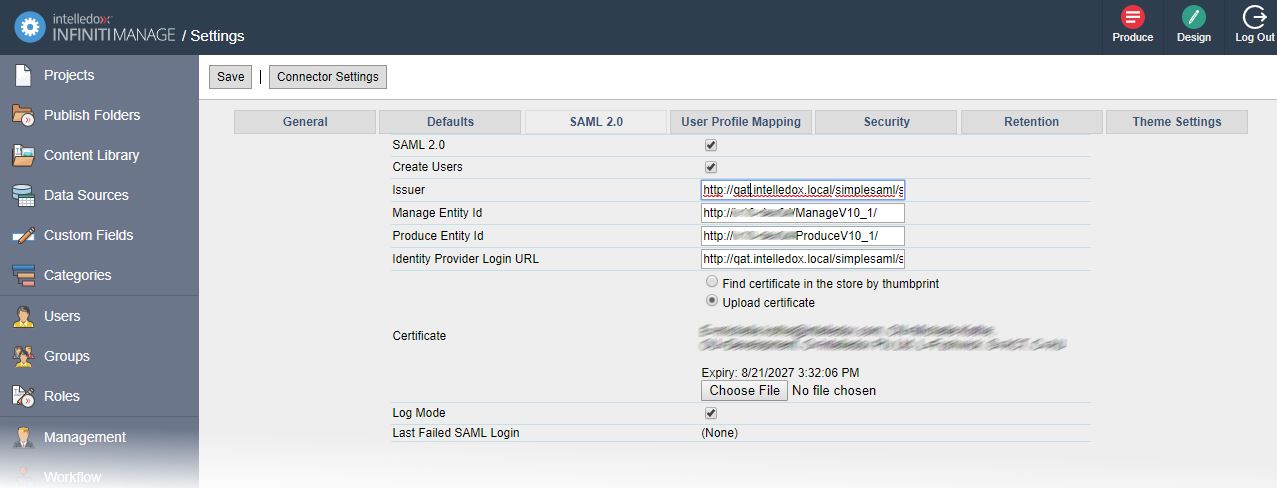
| Setting | Description | Example |
|---|---|---|
| Create Users | An option if to actually create a user in the Infiniti platform. Necessary for any form that involves workflow and is useful for tracking and auditing | Usually checked |
| Issuer | The Issuer ID of the Identity Provider | http://openam.example.com:8080/openam |
| Manage Entity Id | The Entity Id of the Manage Service Provider | Manage, ManageTest, ManageProd Etc. |
| Produce Entity Id | The Entity Id of the Produce Service Provider | Produce, ProduceTest, ProduceProd Etc. |
| Identity Provider Login URL | The URL of the Single Sign on Service URL that Infiniti will make the HTTP-Post Request to. | http://openam.example.com:8080/openam/SSOPOST/metaAlias/idp |
| Certificate | The certificate Infiniti will use to check the signature received in the HTTP-POST Response. A certificate can be installed on the server and referenced by a thumpprint or uploaded directly to the application. | N/A |
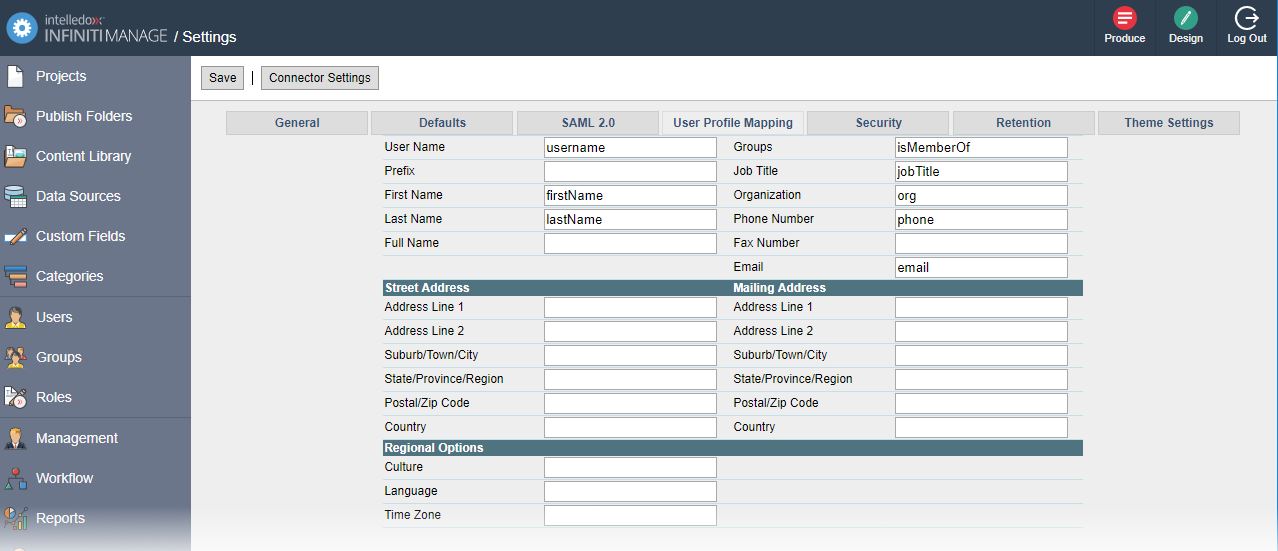
Step 3 - User profile Mapping
As attributes specified in a SAML response are arbitrary it is necessary to map particular user profile fields to the values provided in the SAML response.
- Navigate to the User Profile Mapping Tab.
- Provide at least the name of the attribute where the user’s Group Memberships are specified.
- Optionally specify any other user fields. See Appendix B for a complete list of available Mapping fields
- Save
Step 4 Test
- Close all browsers to ensure any existing Infiniti Sessions are removed.
- Open a new browser and navigate to Infiniti Manage or Produce.
- Infiniti will attempt to create a SAML session as per the settings configured above. You should either be redirected to the Produce/Manage Home Page or the Identify Provider’s Login screen should you not already have an existing session.
Logging and Troubleshooting
When attempting SAML 2.0 authentication Infiniti makes a HTTP-POST request to the identity provider and awaits a response. If both the request and response are successfully made and received Infiniti will log any errors occurred whilst processing the response in the database (for example a failure when checking).
With the logging setting in step 2 above enabled. Logs can be retrieved from the Infiniti database using the following SQL query.
SELECT *
FROM EventLog
ORDER BY DateTime DESC
Where reconfiguration is required SAML 2.0 authentication can be rolled back via the database using the SQL query below. Note the query is appropriate for single tenant environments only.
UPDATE Business_Unit
SET SamlEnabled = 0
WHERE Business_Unit_Guid = '0CC2007E-3344-4059-B368-9BAD2B9BD42B'
SAML 2.0 AUTHENTICATION START
UTCTime: 12/20/2017 4:17:42 AM
Relay State: 0cc2007e-3344-4059-b368-9bad2b9bd42b
Business Unit: 0cc2007e-3344-4059-b368-9bad2b9bd42b
Loading SAML Response
LOGIN STATUS
Login Status urn:oasis:names:tc:SAML:2.0:status:Success
ASSERTION NODE
CONDITIONS
TIME RANGE CHECK
NotBefore:12/20/2017 4:17:12 AM
Now:12/20/2017 4:17:42 AM
NotOnOrAfter:12/20/2017 4:22:42 AM
Time Range OK
ISSUER
Issuer OK
SIGNATURE VALIDATION
Checking response node for signature. + (samlp:Response/ds:Signature)
Signature found
CERTIFICATE LOAD
Loading uploaded certificate
Certificate loaded "[email protected], CN=blah, OU=Development, O=Intelledox Pty Ltd, L=Fyshwick, S=ACT, C=AU"
SIGNATURE CHECK
Signature check OK
USER SYNC
Attribute Names: username, firstName, lastName, isMemberOf, email, jobTitle, org, phone
USERNAME
Get username from mapping
Field Mapping - USERNAME to username (saml:AttributeStatement/saml:Attribute[@Name='username']).
username found
USER PROFILE
Field Mapping - EMAIL to email (saml:AttributeStatement/saml:Attribute[@Name='email']).
email found
Field Mapping - FIRSTNAME to firstName (saml:AttributeStatement/saml:Attribute[@Name='firstName']).
firstName found
Field Mapping - JOBTITLE to jobTitle (saml:AttributeStatement/saml:Attribute[@Name='jobTitle']).
jobTitle found
Field Mapping - LASTNAME to lastName (saml:AttributeStatement/saml:Attribute[@Name='lastName']).
lastName found
Field Mapping - ORGANISATION to org (saml:AttributeStatement/saml:Attribute[@Name='org']).
org found
Field Mapping - PHONENUMBER to phone (saml:AttributeStatement/saml:Attribute[@Name='phone']).
phone found
Update User Group Subscriptions
Field Mapping - GROUPS to isMemberOf (saml:AttributeStatement/saml:Attribute[@Name='isMemberOf']).
Found value: samlUser
Found value: SAML users
Found value: Domain Users
Group Common Name (CN) Conversion: samlUser
Common Name: samlUser
Group Common Name (CN) Conversion: SAML users
Common Name: SAML users
Group Common Name (CN) Conversion: Domain Users
Common Name: Domain Users
Membership Check :Domain Users
Subscribe user to group: Domain Users
Membership Check :IxSupport
User not a member of group: IxSupport
SUCCESS
Appendix A Example SAML Request and Response
Request
<?xml version=1.0 encoding=UTF-8?>
<samlp:AuthnRequest xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol" ID="_fd6b794b-3f77-4529-bc70-b4839fb82f86" Version="2.0" IssueInstant="2016-02-26T03:46:13.057Z" ProtocolBinding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST">
<saml:Issuer xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion">Manage</saml:Issuer>
<samlp:NameIDPolicy Format="urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified" />
</samlp:AuthnRequest>
Response
<samlp:Response xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol" Destination="http://ix10-simonp/ManageV9_3/SamlAuthenticate.aspx" ID="s20ba81f0f7d8dac0a377109c03787e2ea585297c7" InResponseTo="_f9a49ee4-143b-4d15-a2fe-0d431a3d09c7" IssueInstant="2016-02-26T03:52:00Z" Version="2.0">
<saml:Issuer xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion">http://openam.example.com:8080/openam</saml:Issuer>
<ds:Signature xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
<ds:SignedInfo>
<ds:CanonicalizationMethod Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#" />
<ds:SignatureMethod Algorithm="http://www.w3.org/2000/09/xmldsig#rsa-sha1" />
<ds:Reference URI="#s20ba81f0f7d8dac0a377109c03787e2ea585297c7">
<ds:Transforms>
<ds:Transform Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature" />
<ds:Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#" />
</ds:Transforms>
<ds:DigestMethod Algorithm="http://www.w3.org/2000/09/xmldsig#sha1" />
<ds:DigestValue>LYUM7JsNmj4ds9wvdypXjJ4tOJM=</ds:DigestValue>
</ds:Reference>
</ds:SignedInfo>
<ds:SignatureValue>
UJFiE3TyM82NjCi6QOUQjdTZQiaVcKkpwyxKah0PXQe/i/ZWl+vKduLFVDXDPGP5gVrZoKKtEDWr
xDoGCE6UUNruQD85zWdVNO0D0LIHLM/j6+1+myvWP7uTv1/BPlYcQ2Owb34diPmOwN/jeBd/AX3f
1F4faB55Qo9JGiLCANU=
</ds:SignatureValue>
<ds:KeyInfo>
<ds:X509Data>
<ds:X509Certificate>
MIICQDCCAakCBEeNB0swDQYJKoZIhvcNAQEEBQAwZzELMAkGA1UEBhMCVVMxEzARBgNVBAgTCkNh
bGlmb3JuaWExFDASBgNVBAcTC1NhbnRhIENsYXJhMQwwCgYDVQQKEwNTdW4xEDAOBgNVBAsTB09w
ZW5TU08xDTALBgNVBAMTBHRlc3QwHhcNMDgwMTE1MTkxOTM5WhcNMTgwMTEyMTkxOTM5WjBnMQsw
CQYDVQQGEwJVUzETMBEGA1UECBMKQ2FsaWZvcm5pYTEUMBIGA1UEBxMLU2FudGEgQ2xhcmExDDAK
BgNVBAoTA1N1bjEQMA4GA1UECxMHT3BlblNTTzENMAsGA1UEAxMEdGVzdDCBnzANBgkqhkiG9w0B
AQEFAAOBjQAwgYkCgYEArSQc/U75GB2AtKhbGS5piiLkmJzqEsp64rDxbMJ+xDrye0EN/q1U5Of+
RkDsaN/igkAvV1cuXEgTL6RlafFPcUX7QxDhZBhsYF9pbwtMzi4A4su9hnxIhURebGEmxKW9qJNY
Js0Vo5+IgjxuEWnjnnVgHTs1+mq5QYTA7E6ZyL8CAwEAATANBgkqhkiG9w0BAQQFAAOBgQB3Pw/U
QzPKTPTYi9upbFXlrAKMwtFf2OW4yvGWWvlcwcNSZJmTJ8ARvVYOMEVNbsT4OFcfu2/PeYoAdiDA
cGy/F2Zuj8XJJpuQRSE6PtQqBuDEHjjmOQJ0rV/r8mO1ZCtHRhpZ5zYRjhRC9eCbjx9VrFax0JDC
/FfwWigmrW0Y0Q==
</ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
</ds:Signature>
<samlp:Status xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol">
<samlp:StatusCode Value="urn:oasis:names:tc:SAML:2.0:status:Success" xmlns:samlp="urn:oasis:names:tc:SAML:2.0:protocol">
</samlp:StatusCode>
</samlp:Status>
<saml:Assertion xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion" ID="s27b4cdc935aa3d98c0d727fa2079d9bb0103bd732" IssueInstant="2016-02-26T03:52:00Z" Version="2.0">
<saml:Issuer>http://openam.example.com:8080/openam</saml:Issuer>
<ds:Signature xmlns:ds="http://www.w3.org/2000/09/xmldsig#">
<ds:SignedInfo>
<ds:CanonicalizationMethod Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#" />
<ds:SignatureMethod Algorithm="http://www.w3.org/2000/09/xmldsig#rsa-sha1" />
<ds:Reference URI="#s27b4cdc935aa3d98c0d727fa2079d9bb0103bd732">
<ds:Transforms>
<ds:Transform Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature" />
<ds:Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#" />
</ds:Transforms>
<ds:DigestMethod Algorithm="http://www.w3.org/2000/09/xmldsig#sha1" />
<ds:DigestValue>fnw+2iscOwNy7rTSX8767kMCi6g=</ds:DigestValue>
</ds:Reference>
</ds:SignedInfo>
<ds:SignatureValue>
f4f+iFzRvc5/VSMQLS16xD9vrZeSgDR+GvR7gICnGFK5ZHLa2sYb1l5GiTJJb7VqAvaYA701fbod
otbjVmqmsbf+IZVwictbYj0swWmH1WQ63acRHCHg04LLfIBs0nMfsdQ/lWiO2PO82UaAM2XPbpKO
a1/9DsY2Habpp5qONjE=
</ds:SignatureValue>
<ds:KeyInfo>
<ds:X509Data>
<ds:X509Certificate>
MIICQDCCAakCBEeNB0swDQYJKoZIhvcNAQEEBQAwZzELMAkGA1UEBhMCVVMxEzARBgNVBAgTCkNh
bGlmb3JuaWExFDASBgNVBAcTC1NhbnRhIENsYXJhMQwwCgYDVQQKEwNTdW4xEDAOBgNVBAsTB09w
ZW5TU08xDTALBgNVBAMTBHRlc3QwHhcNMDgwMTE1MTkxOTM5WhcNMTgwMTEyMTkxOTM5WjBnMQsw
CQYDVQQGEwJVUzETMBEGA1UECBMKQ2FsaWZvcm5pYTEUMBIGA1UEBxMLU2FudGEgQ2xhcmExDDAK
BgNVBAoTA1N1bjEQMA4GA1UECxMHT3BlblNTTzENMAsGA1UEAxMEdGVzdDCBnzANBgkqhkiG9w0B
AQEFAAOBjQAwgYkCgYEArSQc/U75GB2AtKhbGS5piiLkmJzqEsp64rDxbMJ+xDrye0EN/q1U5Of+
RkDsaN/igkAvV1cuXEgTL6RlafFPcUX7QxDhZBhsYF9pbwtMzi4A4su9hnxIhURebGEmxKW9qJNY
Js0Vo5+IgjxuEWnjnnVgHTs1+mq5QYTA7E6ZyL8CAwEAATANBgkqhkiG9w0BAQQFAAOBgQB3Pw/U
QzPKTPTYi9upbFXlrAKMwtFf2OW4yvGWWvlcwcNSZJmTJ8ARvVYOMEVNbsT4OFcfu2/PeYoAdiDA
cGy/F2Zuj8XJJpuQRSE6PtQqBuDEHjjmOQJ0rV/r8mO1ZCtHRhpZ5zYRjhRC9eCbjx9VrFax0JDC
/FfwWigmrW0Y0Q==
</ds:X509Certificate>
</ds:X509Data>
</ds:KeyInfo>
</ds:Signature>
<saml:Subject>
<saml:NameID Format="urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified" NameQualifier="http://openam.example.com:8080/openam" SPNameQualifier="Manage">sampleuser</saml:NameID>
<saml:SubjectConfirmation Method="urn:oasis:names:tc:SAML:2.0:cm:bearer">
<saml:SubjectConfirmationData InResponseTo="_f9a49ee4-143b-4d15-a2fe-0d431a3d09c7" NotOnOrAfter="2016-02-26T04:02:00Z" Recipient="http://ix10-simonp/ManageV9_3/SamlAuthenticate.aspx" />
</saml:SubjectConfirmation>
</saml:Subject>
<saml:Conditions NotBefore="2016-02-26T03:42:00Z" NotOnOrAfter="2016-02-26T04:02:00Z">
<saml:AudienceRestriction>
<saml:Audience>Manage</saml:Audience>
</saml:AudienceRestriction>
</saml:Conditions>
<saml:AuthnStatement AuthnInstant="2016-02-26T03:52:00Z" SessionIndex="s2ae61fa7dd0d09dcc262fabac9c6e7d29fcd0d401">
<saml:AuthnContext>
<saml:AuthnContextClassRef>urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport</saml:AuthnContextClassRef>
</saml:AuthnContext>
</saml:AuthnStatement>
<saml:AttributeStatement>
<saml:Attribute Name="givenName">
<saml:AttributeValue xmlns:xs="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:type="xs:string">Sample</saml:AttributeValue>
</saml:Attribute>
<saml:Attribute Name="IsMemberOf">
<saml:AttributeValue xmlns:xs="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:type="xs:string">cn=Sales,ou=groups,dc=openam,dc=forgerock,dc=org</saml:AttributeValue>
<saml:AttributeValue xmlns:xs="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:type="xs:string">cn=Infiniti_Administrator,ou=groups,dc=openam,dc=forgerock,dc=org</saml:AttributeValue>
<saml:AttributeValue="" xmlns:xs="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:type="xs:string">cn=IT,ou=groups,dc=openam,dc=forgerock,dc=org</saml:AttributeValue>
<saml:AttributeValue xmlns:xs="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:type="xs:string">cn=HR,ou=groups,dc=openam,dc=forgerock,dc=org</saml:AttributeValue>
</saml:Attribute>
<saml:Attribute Name="sn">
<saml:AttributeValue xmlns:xs="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:type="xs:string">User</saml:AttributeValue>
</saml:Attribute>
</saml:AttributeStatement>
</saml:Assertion>
</samlp:Response>
Appendix B User Profile Mapping Fields
| Setting | Description |
|---|---|
| User Name | A field to use for the Infiniti Username if the default SAML ‘NameID’ element does not contain a meaningful value. This is a required field. For example, use the email address. |
| Groups | The element to look for the user’s group Memberships |
| Prefix, Job Title, Organization, Last Name, Phone Number, Full Name , Fax Number, Email, Address Line 1, Address Line 2, Suburb/Town/City, State/Province/Region, Postal/Zip Code, Country | Regular address fields |
| Culture | A culture code to use for example en-AU, zh-CN, es, etc |
| Language | A language to use must be supported by Infiniti. Possible values: ar zh-cn zh-tw nl en en-us fr fr-ca de ko pt es * th |
| Time Zone | An appropriate user time zone. Possible Values: Dateline Standard Time UTC-11 Samoa Standard Time Hawaiian Standard Time Alaskan Standard Time Pacific Standard Time (Mexico) Pacific Standard Time US Mountain Standard Time Mountain Standard Time (Mexico) Mountain Standard Time Central America Standard Time Central Standard Time Central Standard Time (Mexico) Canada Central Standard Time SA Pacific Standard Time Eastern Standard Time US Eastern Standard Time Venezuela Standard Time Paraguay Standard Time Atlantic Standard Time Central Brazilian Standard Time SA Western Standard Time Pacific SA Standard Time Newfoundland Standard Time E. South America Standard Time Argentina Standard Time SA Eastern Standard Time Greenland Standard Time Montevideo Standard Time UTC-02 Mid-Atlantic Standard Time Azores Standard Time Cape Verde Standard Time Morocco Standard Time UTC GMT Standard Time Greenwich Standard Time W. Europe Standard Time Central Europe Standard Time Romance Standard Time Central European Standard Time W. Central Africa Standard Time Namibia Standard Time Jordan Standard Time GTB Standard Time Middle East Standard Time Egypt Standard Time Syria Standard Time South Africa Standard Time FLE Standard Time Israel Standard Time E. Europe Standard Time Arabic Standard Time Arab Standard Time Russian Standard Time E. Africa Standard Time Iran Standard Time Arabian Standard Time Azerbaijan Standard Time Mauritius Standard Time Georgian Standard Time Caucasus Standard Time Afghanistan Standard Time Ekaterinburg Standard Time Pakistan Standard Time West Asia Standard Time India Standard Time Sri Lanka Standard Time Nepal Standard Time Central Asia Standard Time Bangladesh Standard Time N. Central Asia Standard Time Myanmar Standard Time SE Asia Standard Time North Asia Standard Time China Standard Time North Asia East Standard Time Singapore Standard Time W. Australia Standard Time Taipei Standard Time Ulaanbaatar Standard Time Tokyo Standard Time Korea Standard Time Yakutsk Standard Time Cen. Australia Standard Time AUS Central Standard Time E. Australia Standard Time AUS Eastern Standard Time West Pacific Standard Time Tasmania Standard Time Vladivostok Standard Time Central Pacific Standard Time New Zealand Standard Time UTC+12 Fiji Standard Time Kamchatka Standard Time * Tonga Standard Time |
SAML authentication in multi tenant environments
Unfortunately, when navigating to the Produce home page, Infiniti does not know which tenancy that should be logged into. The default in a Forms authentication environment is to present the login page.
To allow navigation to a specific tenancy, and therefore to authenticate using SAML instead of forms authentication, Infiniti has the following techniques:
-
When navigating to a specific form, Infiniti is able to determine the tenancy of that form and will, therefore, use the authentication method defined by that tenancy.
-
A TenantId may be used to specify what tenancy to log in to if navigation to the Produce home page is required. The produce homepage in this situation will be the normal home page with "/b/12345" appended to the URL (where the tenant id is 1f0ff6c1-7f29-45fb-9727-1b7b18019f1c). So if Produce is normally http://ixtransform.com then a specific tenancy can be navigated to at http://ixtransform/b/1f0ff6c1-7f29-45fb-9727-1b7b18019f1c.
The easiest way to determine the Tenant Id is via the multi-tenant management portal. Simply click on the tenancy to navigate to the "edit tenant" screen, then examine the URL, which should have something like:
TenantEdit.aspx?ID=1f0ff6c1-7f29-45fb-9727-1b7b18019f1c
on the end. The ID in question is the tenant Id.
Note:
Once a SAML Produce instance is navigated to, a cookie will be stored on that computer and will remember that when accessing that instance of Infiniti, SAML login is preferred. In this situation, in the unlikely situation where forms authentication is desired, the SAML tenancy must be logged out and cookies cleared
Recent Changes
- SAML settings now have a log mode where that captures a more verbose description of what has happens/fails during a SAML authentication and also each SAML authentication (i.e. success and fail).
- SAML 2.0 Settings page has a log Mode check Box
- SAML 2.0 Settings page has the last failed message on display (with a more or less expander),when logging is turned on.
- EventLog Table has all SAML authentication attempts logged. Event level ID is failed/success.
Updated 5 months ago